This is a Pipeline
Shared Library which helps support the use of user-defined inline secrets from
within a Jenkinsfile.
|
Warning
|
This repository hasn’t had a rigorous security evaluation, use at your own risk. |
This Shared Library requires that the Pipeline plugin and Mask Passwords plugin installed.
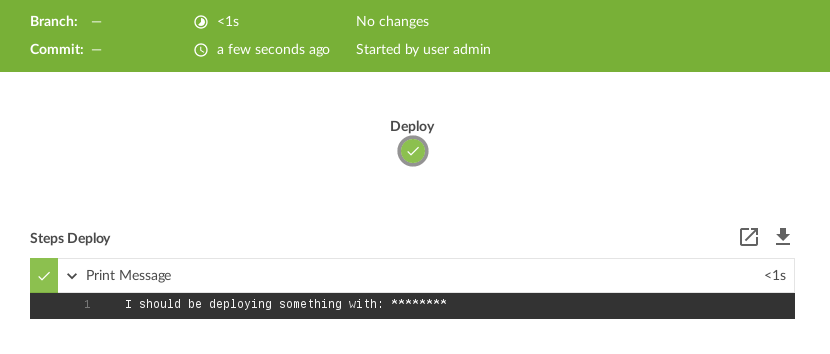
A Pipeline can use secrets similar to environment variables:
Jenkinsfile
node {
stage('Deploy') {
withSecrets(
AWS_SECRET_ID: '{AQAAABAAAAAQWsBycxCz0x8ouOKJLU9OTvHdsN7kt7+6RAcV2zZJTm4=}'
) {
echo "I should be deploying something with: ${env.AWS_SECRET_ID}"
}
}
}