A Semi automatic handy tool to generate YARA rules from sample virus files ( WIP ) for Malware Analyst, inspired by DIFF function of VirusTotal Premium Account.
You can find some sample virus files at https://github.com/YARA-Silly-Silly/sample-malwares
You can find the project repo at https://github.com/YARA-Silly-Silly/yarasilly2
Python3 is required.
- Clone the git repository and enter into the folder
git clone https://github.com/YARA-Silly-Silly/yarasilly2.git
cd yarasilly2
- Create and activate a virtual environment:
Linux
python -m venv venv
source venv/bin/activate
Windows
python -m venv venv
.\venv\Scripts\activate.bat
- Install ssdeep according to your OS from
https://python-ssdeep.readthedocs.io/en/latest/installation.html#installation
Example Ubuntu 20.04
sudo apt-get install build-essential libffi-dev python3 python3-dev python3-pip libfuzzy-dev
- Install the package inside the environment:
pip3 install -r requirements.txt
To start the application check all the options that can be passed to the application using
python yarasilly2.py --help
Config for the application is also present in the file config.ini in the root folder.
Example
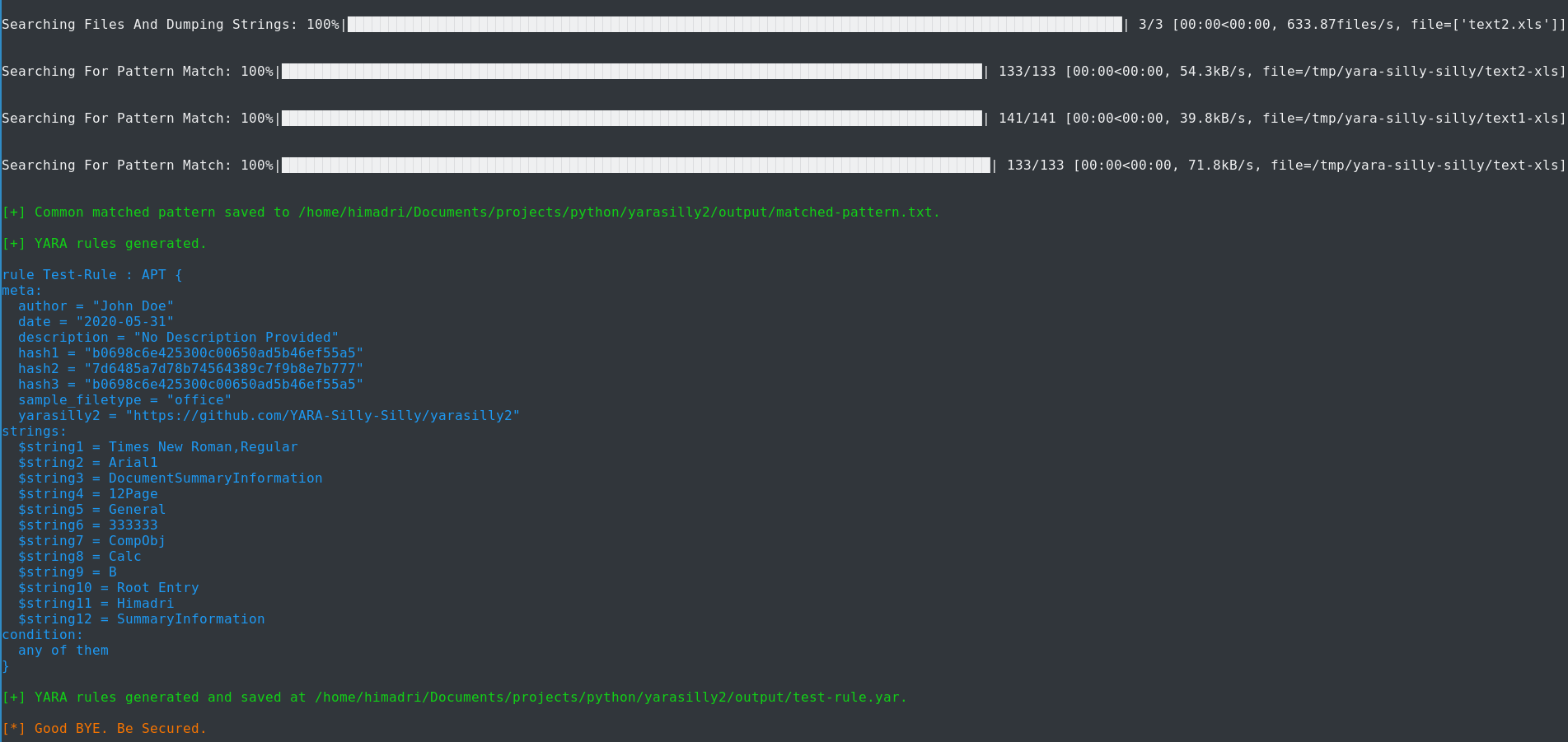
python yarasilly2.py -r "Test-Rule" -t "APT" -a "John Doe" -o 2 -f "office"
The above command will pass the name of the rule Test-Rule, tag APT, author John Doe, pattern occurance 2 and sample file type office.
Using fuzzy match example
python yarasilly2.py -r "Test-Rule" -t "APT" -a "John Doe" -f "office" -fm ./confirm-sample 80 ./probable-sample 60
The above command will pass the name of the rule Test-Rule, tag APT, author John Doe, file type office and then fuzzy match parameters, the first is the confirm malware samples folder, second is the percentage of match between all the files in that folder, third is the probable malware samples folder and fourth one is the percentage of match with the files within the probable folder.
Usage: yarasilly2.py [OPTIONS]
Options:
-r, --rulename TEXT Provide a rule name with no spaces and must
start with letter. [required]
-f, --filetype [office] Select sample set file type choices.
[required]
-m, --matchpatternfile TEXT Matched pattern will be saved to this file.
Please provide full path eg:
./output/matched-pattern
-i, --inputfilepath TEXT File or files will be read from this
location eg: ./files-folder
-fd, --folderdepth INTEGER How much depth within the inputfilepath the
files will be searched. To search all files
with any depth enter 0
-fm, --fuzzymatch <TEXT INTEGER TEXT INTEGER>...
Match file patterns using fuzzy hashing.
Please provide folder path of confirm virus
samples with match percentage of same type
and probable virus samples with should be
matched percent. For eg: -fm ./confirm-
sample 80 ./probable-sample 60
-o, --patternoccurance INTEGER How many match of the pattern within the
files is considered as match.
-b, --block INTEGER File buffer size when reading file.
-l, --loglevel [CRITICAL|ERROR|WARNING|INFO|DEBUG]
Select log level for the application.
[default: ERROR]
-a, --author TEXT Type you name to be filled in the author
field in generate YARA rule. Eg. -n "John
Doe" [default: N/A]
-d, --description TEXT Provide a useful description of the YARA
rule. [default: No Description Provided]
-t, --tags TEXT Apply Tags to Yara Rule For Easy Reference
(AlphaNumeric) [default: ]
--help Show this message and exit. [default:
False]
Yara Silly Silly is maintained by:
Himadri Ganguly |
Krishnendu Paul |
Please see our CONTRIBUTING.md.
Yara Silly Silly is GNU GPL3 licensed. See the LICENSE file for details.