-
Notifications
You must be signed in to change notification settings - Fork 37
Background and Terminology
We recommend that users have a basic understanding of how 802.1x and EAP work in order to use this tool effectively. The following terminology will be used in this document:
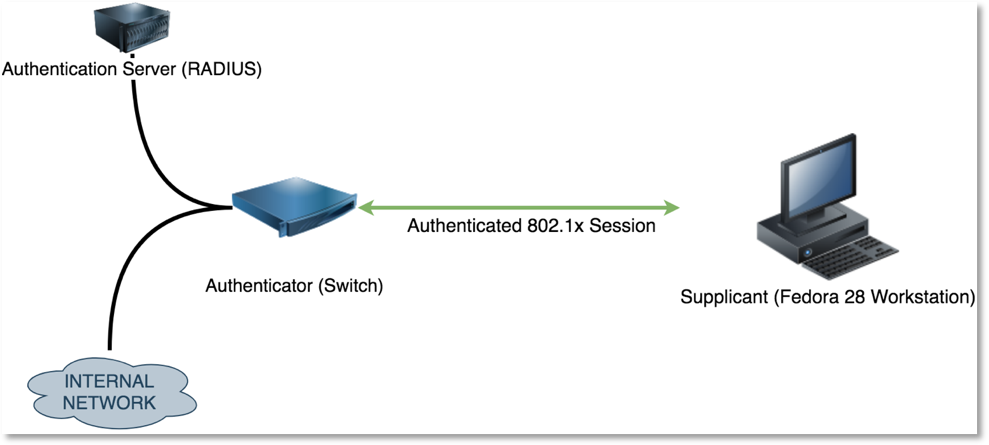
- Authenticator - The switch that provides access to the internal network. Performs authentication on behalf of the authentication server.
- Authentication Server - The host that runs software that implements RADIUS or some other Authorization, Authentication, and Accounting (AAA) protocol.
- Supplicant - The authorized device that is currently connected to the authenticator. Usually a workstation, printer, etc.
The goal of any 802.1x bypass is to be able to connect a rogue device to an authenticated network via the authenticator, in order to interact both passively and dynamically with the network.
The goal of any 802.1x bypass is to be able to connect a rogue device to an authenticated network via the authenticator, in order to interact both passively and dynamically with the network. There are two ways to do this:
Option 1
Effective against: 802.x-2004, 802.1x-2001
Our first option is to introduce the rogue device directly between the authenticator and the supplicant, as shown in the diagram below. This style of bypass is essentially a Man-In-The-Middle (MITM). The rogue device sits transparently on the wire, providing the attacker with the ability to sniff traffic. More sophisticated implementations of this style of attack allow the attacker to interact with the network as well.
To use Silentbridge to perform this style of attack, please refer to Classic 802.1x Bypass.

Option 2
Effective against: 802.1x-2010, 802.x-2004, 802.1x-2001
The second option is to find a way to connect our rogue device directly to the network, as shown in the diagram below. To use Silentbridge to perform this style of attack, please refer to Bait n Switch Attack and Auth Analyzer and EAP Forced Reauthentication Attack.
