-
Notifications
You must be signed in to change notification settings - Fork 435
3.1. Investigating hooks and patches
By default, PE-sieve detects patches and inline hooks in the code of scanned modules. This section describes such case.
Additionally, it may also detect IAT hooks, but it needs to be enabled by additional parameter: /iat - which is described here.
The listing of detected hooks and patches is provided by PE-sieve in form of a file with a .tag extension.
TAG format is a very simple, custom format dedicated to annotate offsets in executable. Its basic form is the following:
{RVA};{comment}
PE-sieve uses this format to annotate offsets in the PE file, where the hooks (or other type of patches) have been discovered.
If the PE-sieve detected any patches, the modified PE file will be dumped along with the accompanying TAG file:
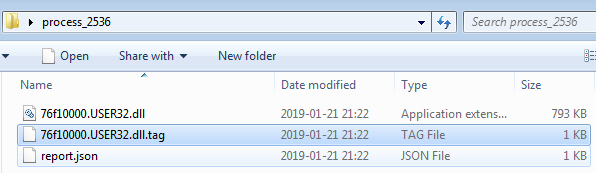
Example of the JSON scan report - noting about the number of patches...
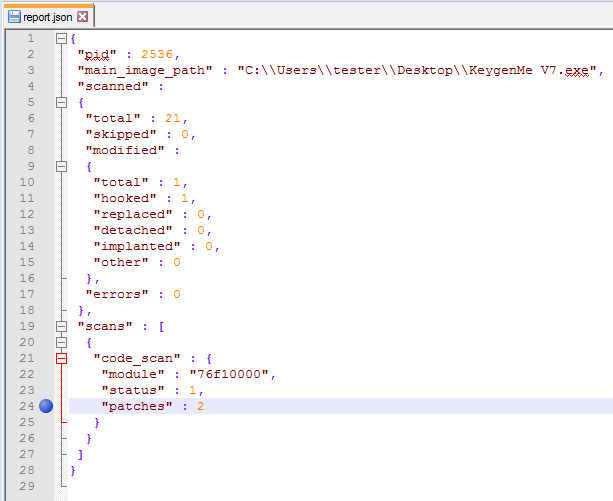
...and a TAG file - describing more details about the found hook/patch, i.e.:
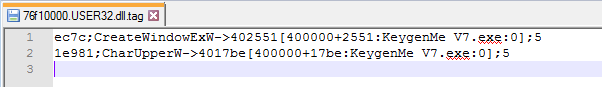
Content of the TAG file:
ec7c;CreateWindowExW->402551[400000+2551:KeygenMe V7.exe:0];5
1e981;CharUpperW->4017be[400000+17be:KeygenMe V7.exe:0];5
Format:
{RVA};{hooked_function}->{VA where the hook leads to}[{details}];{size of the patch}
The {details} are added when the hook redirects execution to some identified module. They include following information:
{module base}+{hook RVA}:{module name}:{is the module identified as suspicious}
For example – in the application presented above, two functions within User32.dll have been hooked: CreateWindowExW and CharUpperW. Their execution was redirected appropriately to offsets 0x402551 and 0x4017be. We can find that those offsets are located in the main module (named KeygenMe V7.exe), that was loaded at the base 0x400000.
Since the file that was patched is also dumped on the disk, we can load it into a disassembler and visit the annotated offsets, to see the hooks/patches in their original context.
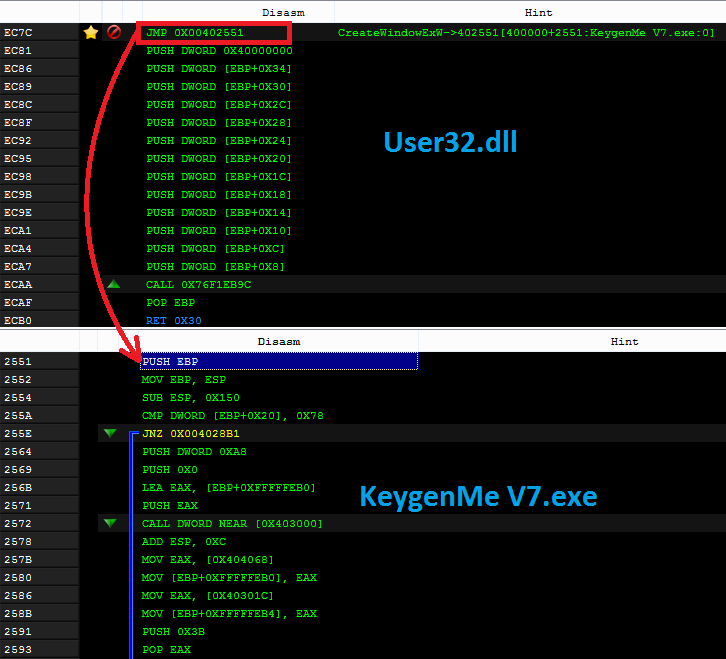
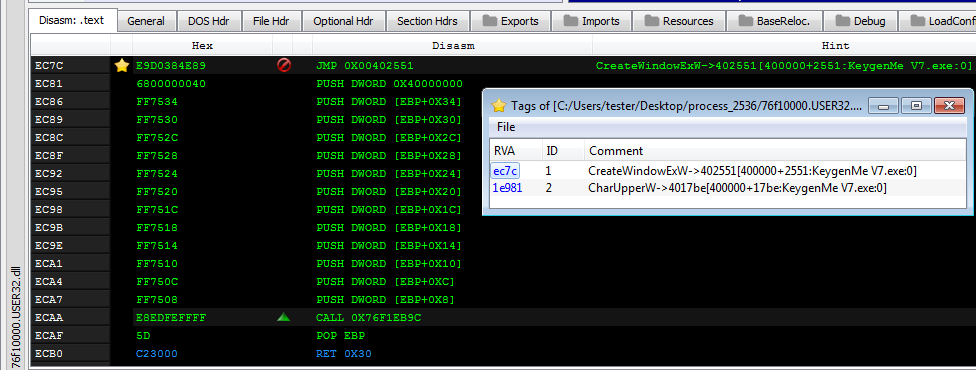
The TAG file can be loaded i.e. into PE-bear. Thanks to this, we can easily browse the found hooks and check the code that was overwritten.
TAG format is natively supported by PE-bear. Once you load the dumped executable into PE-bear, appropriate tag file will be automatically loaded (the only condition is, the TAG file must be located in the same directory as the PE).
You can see the list of all the tags by opening the dedicated panel:
The tagged offsets will be marked with a "star" in the disassembler view:
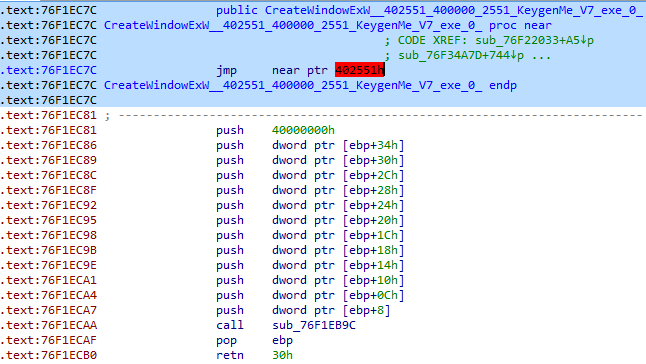
The same TAG file can be also loaded into IDA, with the help of the IFL plugin.
First load the dumped executable, where the hooks/patches have been detected. Open IFL, then click "Load names" that is located at the bottom of the panel:
Then, choose the TAG format from the menu:
And supply the appropriate TAG file. The comments describing patched places will be added into IDA database.
If the hook is installed at the beginning of the function, the name of the function gets annotated, and we can find it using filters in IFL:
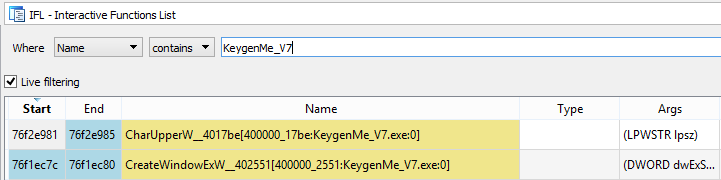
The beginning of the hooked function in IDA: